
Shifting Requirements for Lawful Intelligence in the Era of More Everything
Today’s lawful intelligence measures draw on a long legacy of intercepted communications. And while the days of simple wiretaps are long gone, the foundational idea
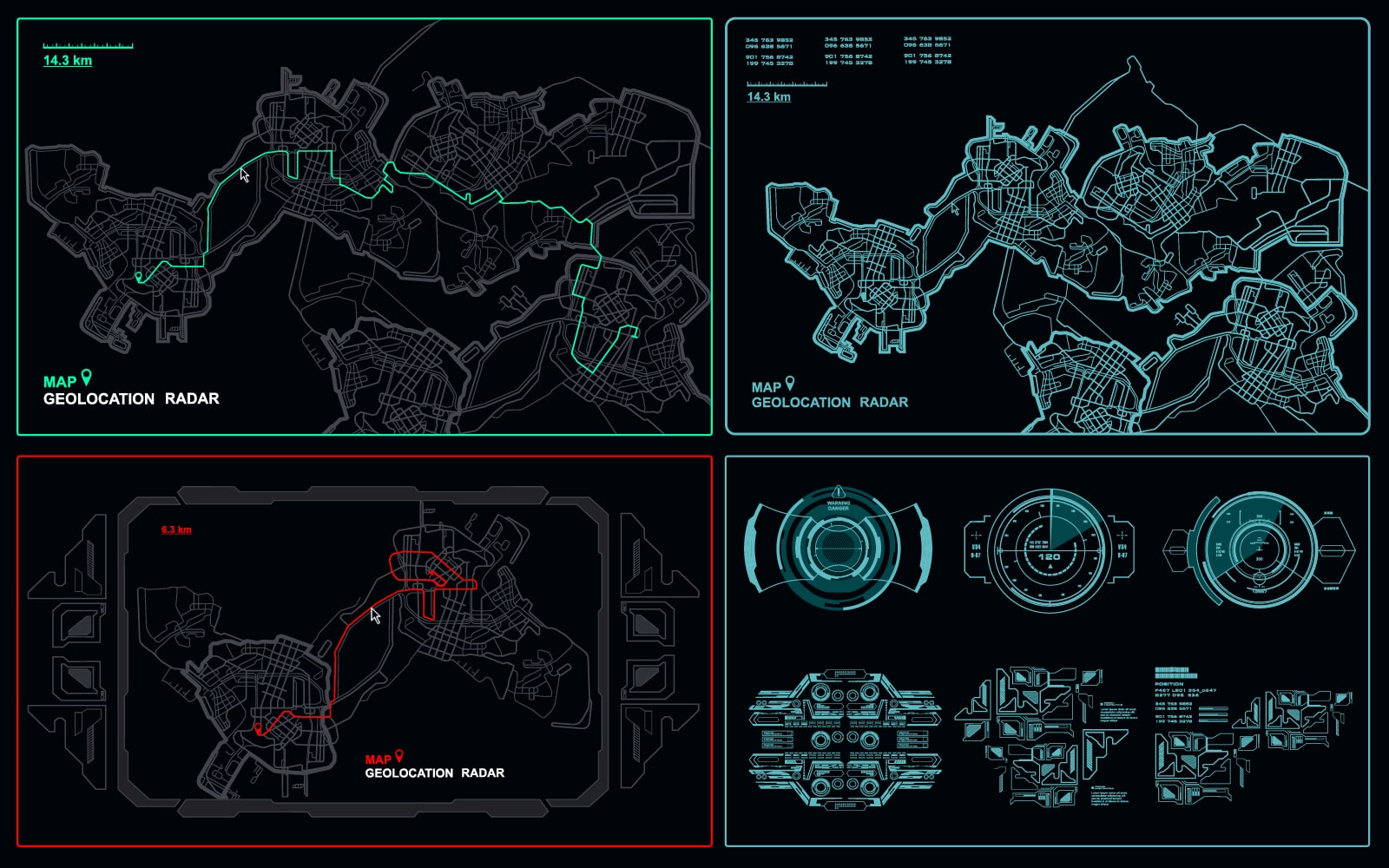
Vertical positioning is critical for location intelligence and emergency response in large, dense urban areas. Longitude and latitude alone are not enough to identify a subject’s position in a multi-story
Quality of Experience (QoE) and Quality of Service (QoS) are at the forefront of every communication service provider’s (CSP) efforts to build a loyal subscriber base. Dropped calls, poor audio quality,
As the scope of digital information generated by subjects and devices of interest continues to grow, law enforcement agencies (LEAs) must evolve their techniques for transforming vast databases of raw
Identifying the physical locations of emergency callers is critical to delivering public safety services. When callers to Public Safety Answering Points (PSAPs) can’t accurately provide their location,
In the past decade, there has been amazing growth in the amount of data available on individuals, their communications, and their patterns of life, but an increasing proportion of that data is encrypted.

Today’s lawful intelligence measures draw on a long legacy of intercepted communications. And while the days of simple wiretaps are long gone, the foundational idea

The massive, ever-growing role of social networks in human communication comes with a unique set of hazards. In particular, the layer of concealment provided by

As the volume, variety, and velocity of data potentially available to lawful intelligence grows exponentially, the control mechanisms that govern its interception become more critical.

Distributed 5G network topologies have forever forced mediation for lawful interception out beyond the network core. As computing moves closer to the subscriber, mediation nodes

Just a tiny fraction of cryptocurrency transactions are related to criminal activity, but they are still a critical mechanism for payment associated with crimes that
Technology developments for telecommunications networks often add more challenges than benefits for lawful intelligence operations. Separating the noise from the signal in massive 5G data

It’s an irony of this moment that, even as 5G networks increase the amount of data on public networks by orders of magnitude, the technology
As communication service providers (CSPs) continue to build out 5G networks, standards-based infrastructure is replacing the proprietary interfaces, formats, and protocols of previous technology generations.

Most telecommunications carriers operate equipment from different generations of technology, and often have multiple vendor environment. Carriers can accrete these layers over time, as their

As unmanned aerial vehicles (UAVs) become more common, they are of growing interest to law enforcement agencies (LEAs). Drones have been widely adopted as part

As 5G networks roll out across the world, law enforcement agencies (LEAs) are being forced to reimagine investigation methods related to lawful intelligence. The types

The metadata that surrounds the data payloads for lawful intelligence intercepts has become as important as the payload data itself. Location data, for example, can

Successive generations of technology continue to enable the discovery, assembly, and analysis of information that plays a key role in every law-enforcement investigation. Digitization helped

The history of lawful intelligence runs a parallel course to the evolution of communications technology, from wiretaps placed on mechanical switches in the last century

We are in an intensive era of cloud adoption by communication service providers (CSPs) for 5G networks. This shift is driven by the need for

The introduction of 5G, high bandwidth services, and new applications mark a new, intensive era of cloud adoption by communication service providers (CSPs) for their

The process of deploying and integrating solutions for lawful interception, handover, and analysis of network data is complex, but well-charted. Looking carefully at previously completed

With the increased attention to information privacy in recent years, a majority of electronic communications are now encrypted. Having that information irretrievably hidden creates novel

As billions of IoT devices are provisioned, their multitude of roles are mirrored by their complex impact on lawful intelligence. Endpoints that range from consumer

The evolution of wide-area networking continues to drive processing out to the network edge. That trend first gained traction with widespread cloud adoption, and it
THE DATA SILO DILEMMA FOR LAW ENFORCEMENT
How to Ingest, Filter and Query 5G Volumes
Webinar Presented by Kevin McTiernan